Introduction
Sogenactif is a secure multi-channel e-commerce payment solution that complies with the PCI DSS standard. It allows you to accept and manage payment transactions by taking into account business rules related to your activity (payment upon shipping, deferred payment, recurring payment, payment in instalments, etc.).
The purpose of this document is to explain the implementation steps of the Sogenactif Paypage POST solution up to live operations.
Who does this document target?
This document is intended for merchants wishing to subscribe to the Sogenactif offer and use a connector based on HTTPS exchanges in POST mode between their websites and the Sogenactif Paypage POST payment servers.
It is an implementation guide for your technical team.
To get an overview of the Sogenactif solution, we advise you to consult the following documents:
- Functional presentation
- Functionality set-up
Prerequisites
Knowledge of standards related to web programming languages used today, such as Java, PHP or .Net, is necessary to develop a connection to Sogenactif Paypage POST.
Secret key management
Upon your subscription, SG provides a secret key on the Portail Sogenactif that will allow you to secure exchanges between your website and the Sogenactif server.
You are responsible for looking after this key and should take all measures to:
- restrict access to the key
- safeguard it by encrypting it
- never copy it onto a non-secure disc or device
- never send it (via e-mail or regular mail) in a non-secure method
A secret key compromised (and used by a malicious third party) might disrupt the regular operation of your shop and might in particular generate unauthorised sales or cash transactions (e.g. refunds).
The very same secret key is used on the various Sogenactif Paypage, Sogenactif Office Serveur, Sogenactif In-App and Sogenactif Walletpage connectors.
keyVersion field with the new
version, otherwise you will get an answer code 34 (suspected
fraud).Contacting the support
For any question or request for technical assistance, you can contact the usual Sogenactif support on 0 825 090 095 (0.15€/min + call charge - rate as of 02/11/2022) from Monday to Friday, from 9am to 7pm, excluding public holidays, or write to supportsogenactif@worldline.com specifying your VAD or MID contract number for a more efficient handling of your request.
Understanding payment with Sogenactif Paypage POST
The general principle for a payment process is as follows:
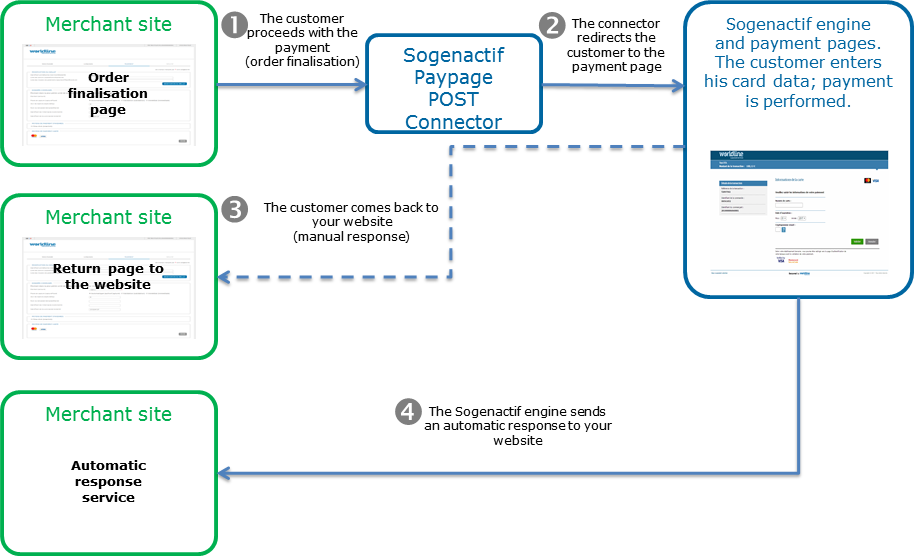
1. When the customer makes a payment, a payment request must be sent to Sogenactif Paypage POST. The URL of this connector is provided by SG. The request is then checked, and quantified if valid (it is named RedirectionData in the system). The request is sent through a POST form via HTTPS. Any other solution that can send such requests also works.
2. Sogenactif Paypage POST redirects the calling application to the Sogenactif payment pages. The customer must enter the information of the means of payment for the Sogenactif payment server to process the transaction. It is worth noting that payment details can be entered directly on the server that provides the means of payment (e.g. PayPal or SEPA mandate). At the end of the payment process, whether successful or not, two responses are created and sent to the URL specified as part of flow No. 1.
There are two independent response notifications:
3. The payment server sends the manual responses in HTTP(S) POST format to the manual response URL. This URL is specified in the payment request and is used when the customer clicks on the Continue button of the payment page. It is the page the user is redirected to at the end of the payment. As nothing guarantees that the customer will click on this link, you have no guarantee of receiving the manual response either.
4. Automatic responses are sent separately from manual responses. They also use the HTTP(S) POST requests sent by the Sogenactif payment servers, this time using the automatic response URL specified in the payment request. This means you receive the reponse as soon as the payment is made on the Sogenactif payment pages.
Getting started with Sogenactif Paypage POST in 5 steps
Step 1: registering the shop
In order to register your shop as live, you are required to complete the registration form sent by SG and to send the form back to SG.
When filling in the form, you must appoint an administrator contact and a technician contact so that SG can send you the information needed to launch your shop.
SG will then register your shop and e-mail you your merchant ID (merchantId), together with your Portail Sogenactif ID and password.
For Portail Sogenactif connection, the contact given in the Sogenactif contract - "Sogenactif Portal" section will receive an e-mail containing the identifier and a link to generate their own password. For Sogenactif Téléchargement connection, the contact given in the Sogenactif contract - section "Sogenactif Download" will receive their password by e-mail, the identifier will be sent by a separate e-mail to the contact indicated for the MEX.
Step 2: making a payment
The payment request is an HTTPS POST request sent to the Sogenactif Paypage POST connector. The request is sent via an HTML form using the POST method.
Generating the payment request
Three mandatory data elements are provided in the payment request.
| Data element name | Description |
|---|---|
| Data | Contains all the information about the transaction. |
| InterfaceVersion | Defines the request version and the response exchanged with the Sogenactif server. |
| Seal | Used to validate the exchanged data integrity. The Seal element is computed using the Data data element and the secret key. |
Additional optional data elements are available:
| Data element name | Description |
|---|---|
| Encode | Specifies the method used to encode the Data field element. |
| SealAlgorithm | Specifies the algorithm used to compute the Seal field element. |
Data field element syntax
The Data field element is structured using the following format:
<fieldName1>=<fieldValue1>|<fieldName2>=<fieldValue2>|…|<fieldNameN>=<fieldValueN>All fields required for the transaction (see details in the data dictionary) should be included in the character string. The order of fields is irrelevant.
Sample payment request with an amount of 55 euros:
amount=5500|currencyCode=978|merchantId=011223744550001|normalReturnUrl=http://www.normalreturnurl.com|transactionReference=534654|keyVersion=1A field can have several values:
..|fieldName=value1,value2, … ,valueX|…Sample paymentMeanBrandList field with VISA and MASTERCARD as values:
…|amount=5500|currencyCode=978|merchantId=011223744550001|normalReturnUrl=http://www.normalreturnurl.com|transactionReference=534654[paymentMeanBrandList=VISA,MASTERCARD|keyVersion=1|…If the field is a container, you should use a full stop between the container name and the field name:
..|Container.fieldName1=fieldValue1|container.fieldName2=fieldValue2|……Sample customerContact field containing customer's e-mail (me@email.com), first name and last name (John Smith):
…|customerContact.email=me@email.com|customerContact.firstname=John|customerContact.lastname=Smith|…If a field contains a list of complex objects, its representation is built using the following format:
..|<field1>=<value1>| <objectName>.<itemName= {<fieldNameA1>=<fieldValueA1>,<fieldNameA2>=<fieldValueA2>}, {<fieldNameB1>=<fieldValueB1>,<fieldNameB2>=<fieldValueB2>}, {<fieldNameC1>=<fieldValueC1>,<fieldNameC2>=<fieldValueC2>}| <fieldName2>=<fieldValue2>|……Sample payment request with a list of complex objects for the shoppingCartDetail field, containing three products named apple, mango and pear:
amount=5500|currencyCode=978|merchantId=011223744550001|normalReturnUrl=http://www.normalreturnurl.com
|transactionReference=534654|shoppingCartDetail.shoppingCartItemList={productName=apple,
productDescription=red},{productName=pear,productDescription=green},{productName=mango,productDescription=yellow}|keyVersion=1Encoding the Data field
The Data field should be encoded using base64 or base64Url if it contains special characters (such as accented characters).
Request fields presence
Some fields of the payment request are required:
- Only when using certain means of payment. Please read the dedicated means of payment guide to know the mandatory fields.
- Depending on your shop configuration. Please read the Functionality set-up to find out the mandatory fields.
- Only in certain use cases (e.g. recurring payment). Please read the Functionality set-up to know the mandatory fields.
Those fields are marked as "conditional".
Securing the request
The request includes the transaction parameters and is sent by the customer's web browser. Theoretically, a third party can intercept the request and modify its content before the data reaches the payment server.
Therefore it is necessary to strengthen security so as to ensure the integrity of the parameters of the transaction sent. The Sogenactif solution meets this challenge by exchanging signatures. An effective signature control comprises two elements:
- the integrity of the request and response messages
- the issuer and recipient authentication, as they share the same secret key
How to secure the request
The request is secured by calculating the hash value in line with the transaction parameters. Then, the secret key is added to it. All character strings are converted to UTF-8 before being hashed.
The hashing algorithm generates an irreversible result. When such a message is received, the recipient needs to recalculate the hash value and compare it with the one received. Any difference indicates that the data exchanged was falsified, or that the recipient and the issuer do not share the same secret key.
The result must be sent in hexadecimal format in the data element named Seal.
Calculating the Seal data element
HMAC-SHA algorithm
The value of the Seal data element is computed as follows:
- Content of the Data field sent in the POST form. Giving the data, mentioned in the examples below.
- UTF-8 encoding of data from the previous result.
- HMAC with SHA256 encryption of bytes obtained with the secret key.
This procedure can be summarised as follows:
HMAC-SHA256( UTF-8(Data), UTF-8(secretKey))For the seal to be computed with the HMAC-SHA-256
algorithm, the use of which we strongly recommend, the input
parameters of the request must include the sealAlgorithm field populated with the
following value: “HMAC-SHA-256”.
Hmac Sha256 sample code
- Sample Hmac Sha256 encoding in Php 5
<?php … // Seal computation thanks to hash sorted data hash with merchant key $data_to_send= utf8_encode($data) $seal=hash_hmac('sha256', $data_to_send, $secretKey); … … ?>data_to_send and secretKey must use a UTF-8 character set. Please refer to the utf8_encode function for the conversion of ISO-8859-1 characters in UTF-8.
- Sample Hmac Sha256 encoding in Java
import java.security.InvalidKeyException; import java.security.NoSuchAlgorithmException; import javax.crypto.Mac; import javax.crypto.spec.SecretKeySpec; public class ExampleHMACSHA256 { /** * table to convert a nibble to a hex char. */ static final char[] hexChar = { '0' , '1' , '2' , '3' , '4' , '5' , '6' , '7' , '8' , '9' , 'a' , 'b' , 'c' , 'd' , 'e' , 'f'}; /** * Fast convert a byte array to a hex string * with possible leading zero. * @param b array of bytes to convert to string * @return hex representation, two chars per byte. */ public static String encodeHexString ( byte[] b ) { StringBuffer sb = new StringBuffer( b.length * 2 ); for ( int i=0; i<b.length; i++ ) { // look up high nibble char sb.append( hexChar [( b[i] & 0xf0 ) >>> 4] ); // look up low nibble char sb.append( hexChar [b[i] & 0x0f] ); } return sb.toString(); } /** * Computes the seal * @param Data the parameters to cipher * @param secretKey the secret key to append to the parameters * @return hex representation of the seal, two chars per byte. */ public static String computeSeal(String data, String secretKey) throws Exception { Mac hmacSHA256 = Mac.getInstance("HmacSHA256"); SecretKeySpec keySpec = new SecretKeySpec(secretKey.getBytes(), "HmacSHA256"); hmacSHA256.init(keySpec); return encodeHexString(hmacSHA256.doFinal(data.getBytes())); } /** * @param args */ public static void main(String[] args) { try { System.out.println (computeSeal("parameters", "key")); } catch (Exception e) { e.printStackTrace(); } } } - Sample Hmac Sha256 encoding in .net
(Carried out using a simple form called "Form1" containing two text fields to enter data and txtSecretKey, and another field to display lblHEX).
using System; using System.Collections.Generic; using System.ComponentModel; using System.Data; using System.Drawing; using System.Text; using System.Windows.Forms; using System.Security.Cryptography; namespace ExampleDotNET { public partial class Form1 : Form { public Form1() { InitializeComponent(); } private void cmdGO_Click(object sender, EventArgs e) { String sChaine = data.Text; UTF8Encoding utf8 = new UTF8Encoding(); Byte[] encodedBytes = utf8.GetBytes(sChaine); byte[] shaResult; HMAC hmac = new HMAC.Create("HMACSHA256"); var key = "YourSecretKey"; hmac.Key = utf8.GetBytes(key); hmac.Initialize(); shaResult = hmac.ComputeHash(encodedBytes); lblHEX.Text = ByteArrayToHEX(shaResult); } private string ByteArrayToHEX(byte[] ba) { StringBuilder hex = new StringBuilder(ba.Length * 2); foreach (byte b in ba) hex.AppendFormat("{0:x2}", b); return hex.ToString(); } } }
Seal calculation validation
Once you have set up your seal calculation, here is a sample request to help you verify that you find the correct seal:
automaticResponseURL=https://automatic-response-url.fr/|normalReturnURL=https://normal-return-url/|captureDay=0|captureMode=AUTHOR_CAPTURE|merchantId=011223344550000|amount=2500|orderId=ORD101|currencyCode=978|transactionReference=TREFEXA2012|keyVersion=1|transactionOrigin=SO_WEBAPPLI|returnContext=ReturnContext|orderChannel=INTERNET|customerContact.email=customer@email.comFor the above request, with a SHA-256 hash algorithm and the following secret key:
secret123The expected seal is:
ac2332b57a674aba5b28a03dae677fa2f4c1ae8a349ebbdd6772a098c7f29861SHA-256 algorithm
The value of the Seal data
element is computed as follows:
- Concatenation of the
Datafield element and of the secret key (encoded if the corresponding option is selected). - UTF-8 encoding of the data constituting the result of the previous operation.
- SHA256 hashing of bytes obtained.
This procedure can be summarised as follows:
SHA256( UTF-8(Data+secretKey ) )Sample Sha256 code
- Sample Sha256 encoding in Php 5
<?php
echo hash('sha256', $data.$secretKey);
?> The UTF-8 character set should be used for the Data and secretKey data. To convert ISO-8859-1 to UTF-8, use the utf8_encode function.
- Sample Sha256 encoding in Java
import java.security.MessageDigest;
public class ExampleSHA256 {
/**
* table to convert a nibble to a hex char.
*/
static final char[] hexChar = {
'0' , '1' , '2' , '3' ,
'4' , '5' , '6' , '7' ,
'8' , '9' , 'a' , 'b' ,
'c' , 'd' , 'e' , 'f'};
/**
* Fast convert a byte array to a hex string
* with possible leading zero.
* @param b array of bytes to convert to string
* @return hex representation, two chars per byte.
*/
public static String encodeHexString ( byte[] b )
{
StringBuffer sb = new StringBuffer( b.length * 2 );
for ( int i=0; i<b.length; i++ )
{
// look up high nibble char
sb.append( hexChar [( b[i] & 0xf0 ) >>> 4] );
// look up low nibble char
sb.append( hexChar [b[i] & 0x0f] );
}
return sb.toString();
}
/**
* Computes the seal
* @param Data the parameters to cipher
* @param secretKey the secret key to append to the parameters
* @return hex representation of the seal, two chars per byte.
*/
public static String computeSeal(String Data, String secretKey) throws Exception
{
MessageDigest md = MessageDigest.getInstance("SHA-256");
md.update((Data+secretKey).getBytes("UTF-8"));
return encodeHexString(md.digest());
}
/**
* @param args
*/
public static void main(String[] args) {
try {
System.out.println (computeSeal("parameters", "key"));
} catch (Exception e) {
e.printStackTrace();
}
}
}- Sample Sha256 encoding in .NET
Completed using a simple form called "Form 1" containing two text fields to be filled in: data, txtSecretKey and another one to be displayed: lblHEX.
using System;
using System.Collections.Generic;
using System.ComponentModel;
using System.Data;
using System.Drawing;
using System.Text;
using System.Windows.Forms;
using System.Security.Cryptography;
namespace ExampleDotNET
{
public partial class Form1 : Form
{
public Form1()
{
InitializeComponent();
}
private void cmdGO_Click(object sender, EventArgs e)
{
String sChaine = data.Text + txtSecretKey.Text;
UTF8Encoding utf8 = new UTF8Encoding();
Byte[] encodedBytes = utf8.GetBytes(sChaine);
byte[] shaResult;
SHA256 shaM = new SHA256Managed();
shaResult = shaM.ComputeHash(encodedBytes);
lblHEX.Text = ByteArrayToHEX(shaResult);
}
private string ByteArrayToHEX(byte[] ba)
{
StringBuilder hex = new StringBuilder(ba.Length * 2);
foreach (byte b in ba)
hex.AppendFormat("{0:x2}", b);
return hex.ToString();
}
}
}Processing payment initialisation errors
All fields received by Sogenactif Paypage POST through the connector are checked individually. The table below lists the error messages that might be displayed during this step, and the solutions to be implemented.
| Message | Root | Solution |
|---|---|---|
Unknown version interface: <version> |
The <version> value in the InterfaceVersion field is unknown. | Check the interface version in this user guide (the current version is HP_2.57). |
Invalid keyword: <fieldName>= <field value> |
The <fieldName> field is not expected in the payment request. | Check the field names in the following chapter and in the Data dictionary. |
Invalid field size: <fieldName>= <field value> |
The <fieldName> field is of incorrect length. | Check the field length in the Data dictionary. |
Invalid field value: <fieldName >= <field value> |
The <fieldName> field value is incorrect. | Check the available field values in the Data dictionary. |
Mandatory field missing: <fieldName> |
The <fieldName> field is missing in the payment request. | Please read the following chapter to check the mandatory fields in the payment request. |
Unknown security version: <version> |
The <version> value of the keyVersion field is unknown. | Check the available key versions in Sogenactif Téléchargement. |
Invalid signature |
The payment request seal checking has failed. This may be caused by an incorrect computing of the Seal data or may indicate the alteration of some fields after the signature was computed. | Check that the computing of the Seal is carried out as described in the previous chapter. If it is, ask for a secret key change via Sogenactif Téléchargement because the request has been altered. |
Transaction already processed: <transaction reference> |
A payment request with the same transactionReference has already been received and processed by the Sogenactif servers. | Check if the transactionReference field value is unique for the relevant transaction. |
<Other messages> |
In the case of technical errors, various messages may appear. | Please get in touch with the technical support. |
Populating the request fields
The request and the response of paymentWebInit method are described in this page.
Setting up the payment request
Here is an example of how to set up the payment request for each functionality available in Sogenactif Paypage POST (the details of these functionalities are described in the Functionality set-up guide).
Dynamic display of the means of payment
You need to use the paymentMeanBrandList field to filter the means of payment that will be displayed on the means of payment selection page:
..|paymentMeanBrandList=VISA,PAYPAL|..Receipt display by Sogenactif
The payment confirmation page that Sogenactif displays by default can be deactivated using the paypageData.bypassReceiptPage field:
..|paypageData.bypassReceiptPage=Y|..Payment channel
To choose your payment channel, you must fill in the orderChannel field in the payment request:
…|orderChannel= INTERNET|..End-of-day payment
For end-of-day payments, simply fill in the captureMode and captureDay fields:
…|captureDay=0|captureMode=AUTHOR_CAPTURE|..Deferred payment
For payments that must be captured N days after they were accepted online, simply fill in the captureMode and captureDay fields (3 days in the following example):
…|captureDay=3|captureMode=AUTHOR_CAPTURE|..For more complex cases of deferred payments, such as multiple shipments or shipment beyond 6 days, please refer to the "multiple payment on dispatch" guide.
Payment upon shipping
For payments upon shipping, the transaction is captured during your validation. You just need to fill in the captureMode and captureDay fields (in the following example, a period of up to 3 days before the validation is set):
…|captureDay=3|captureMode=VALIDATION|..Payment in instalments
For payments with instalments linked to a very same transaction, you need to populate the paymentPattern field with the INSTALMENT value and provide details about instalments in the instalmentData field (in the following example, €600 paid in 3 instalments) :
…|amount=60000|…|transactionReference=tref1|…|paymentPattern=INSTALMENT|instalmentData.number
=3|instalmentData.datesList=20170412,20170512,20170612|instalmentData.transactionReferencesList
=tref1,tref2,tref3|instalmentData.amountsList=10000,30000,20000|..Immediate payment
For immediate payment (available with certain means of payment only), the transaction is paid for during the online authorisation:
…|captureMode=IMMEDIATE|..Multicurrency acceptance
For multicurrency transactions, the currency code must be specified in the request. The payment currency is specified in the acquiring contract.
…|currencyCode=840|..Payment in foreign currencies
Acceptance and payment are carried out in the same currency, which must be specified in the request. Payment in foreign currencies is an option of the acquiring contract.
…|currencyCode=826|..Dynamic Currency Conversion (DCC)
If a Dynamic Currency Conversion (DCC) service is used, the reference currency code must be specified:
…|currencyCode=978|..One Clic registration and payment
For One Clic payments, the customer's wallet ID must be provided in the merchantWalletId field.
…|merchantWalletId=1205987|..Response processing
There are two types of responses. Although the protocol, format and content of both responses are identical, the latter must be managed differently because they meet different needs.
Responses are HTTP(S) POST responses sent to the normalReturnUrl (mandatory) and automaticResponseUrl (optional) URLs specified in the request.
You must set up the system that will decode these responses so you can know the result of the request.
The following four data are defined in the responses:
| Field name | Comments/rules |
|---|---|
| Data | Fields concatenation in the response. |
| Encode | Type of encoding used to encode the Data field. This field is populated using the responseEncoding field from the request. |
| Seal | Response message signature. |
| InterfaceVersion | Connector interface version. |
If the value of the Encode field is “base64” or “base64url”, the Data field must be encoded using Base64/Base64Url so the concatenated string of fields is reconstructed. The concatenated string is structured as follows: key1=value1|key2=value2, etc. The seal (Seal field) of both responses is hashed with the same algorithm as the one supplied as input in the sealAlgorithm field. If no value was defined, SHA-256 is used by default.
The value of the Seal field is computed as follows:
For the HMAC-SHA algorithm:
- use of the shared secret key to generate the HMAC variant of the message
- use of the Data field only (encoded if the corresponding option is selected)
- UTF-8 encoding of the data constituting the result of the previous operation
- HMAC-SHA hashing of the bytes obtained
This procedure can be summarised as follows:
HMAC-SHA256( UTF-8(Data), UTF-8(secretKey))Example of computed Seal with a secret key equal to "secret123" and the Data field in POST format below:
captureDay=0|captureMode=AUTHOR_CAPTURE|currencyCode=978|merchantId=039000254447216|orderChannel=INTERNET|responseCode=00|transactionDateTime=2022-11-14T11:21:12+01:00|transactionReference=SIM20221114112037|keyVersion=1|acquirerResponseCode=00|amount=1000|authorisationId=664865|guaranteeIndicator=N|panExpiryDate=202401|paymentMeanBrand=VISA|paymentMeanType=CARD|customerIpAddress=10.78.106.18|maskedPan=############0600|holderAuthentRelegation=N|holderAuthentStatus=NOT_PARTICIPATING|tokenPan=490700h719850600|transactionOrigin=SIMS|paymentPattern=ONE_SHOT|customerMobilePhone=null|mandateAuthentMethod=null|mandateUsage=null|transactionActors=null|mandateId=null|captureLimitDate=20221114|dccStatus=null|dccResponseCode=null|dccAmount=null|dccCurrencyCode=null|dccExchangeRate=null|dccExchangeRateValidity=null|dccProvider=null|statementReference=null|panEntryMode=MANUAL|walletType=null|holderAuthentMethod=NO_AUTHENT_METHOD|holderAuthentProgram=3DS_V2|paymentMeanId=null|instalmentNumber=null|instalmentDatesList=null|instalmentTransactionReferencesList=null|instalmentAmountsList=null|settlementMode=null|mandateCertificationType=null|valueDate=null|creditorId=null|acquirerResponseIdentifier=null|acquirerResponseMessage=null|paymentMeanTradingName=null|additionalAuthorisationNumber=null|issuerWalletInformation=null|s10TransactionId=6|s10TransactionIdDate=20221114|preAuthenticationColor=null|preAuthenticationInfo=null|preAuthenticationProfile=null|preAuthenticationThreshold=null|preAuthenticationValue=null|invoiceReference=null|s10transactionIdsList=null|cardProductCode=F|cardProductName=VISA CLASSIC|cardProductProfile=C|issuerCode=00000|issuerCountryCode=GRC|acquirerNativeResponseCode=00|settlementModeComplement=null|preAuthorisationProfile=null|preAuthorisationProfileValue=null|preAuthorisationRuleResultList=[{"ruleCode":"VI","ruleType":"NG","ruleWeight":"I","ruleSetting":"S","ruleResultIndicator":"0","ruleDetailedInfo":"TRANS=1:3;CUMUL=24999:200000"},{"ruleCode":"RCode","ruleType":"RType","ruleWeight":"RWeight","ruleSetting":"RSetting","ruleResultIndicator":"RIndicator","ruleDetailedInfo":"DetailedInfo"}]|preAuthenticationProfileValue=null|preAuthenticationRuleResultList=null|paymentMeanBrandSelectionStatus=NOT_APPLICABLE|transactionPlatform=PROD|avsAddressResponseCode=null|avsPostcodeResponseCode=null|customerCompanyName=null|customerBusinessName=null|customerLegalId=null|customerPositionOccupied=null|paymentAttemptNumber=1|holderContactEmail=null|installmentIntermediateServiceProviderOperationIdsList=null|holderAuthentType=null|acquirerContractNumber=3863090010|secureReference=null|authentExemptionReasonList=null|paymentAccountReference=a667b63d8bec4fb980106497c53e4|schemeTransactionIdentifier=b4e683c1a6ff4a09a0415116a0a25b401d38c19d24e643078d|guaranteeLimitDateTime=null|paymentMeanDataProvider=null|virtualCardIndicator=N|cardProductUsageLabel=CREDIT|authorisationTypeLabel=TRANSACTION DE PAIEMENT|authorMessageReference=272612|acceptanceSystemApplicationId=142000000001|challengeMode3DS=null|issuingCountryCode=GRC|abortedProcessingStep=null|abortedProcessingLocation=nullThe Seal you have to obtain is c946655cce0059124b4ad3eb62c0922c51a0a7d8d28a3cf223e4c0da41bbc5b9
Example of computed Seal with a secret key equal to "secret123" and the Data field in JSON format below:
{"keyVersion":1,"amount":44000,"captureDay":0,"captureMode":"AUTHOR_CAPTURE","currencyCode":"978","customerId":"40813","customerIpAddress":"213.118.246.190","merchantId":"225005049920001","orderAmount":44000,"orderChannel":"INTERNET","responseCode":"97","responseDescription":"Request time-out; transaction refused","transactionDateTime":"2023-03-15.00:39:04+0100","transactionReference":"dd88adfZ1027b40813f40813y1678837075","statementReference":"T7Ft4KKLRA2M11B9","s10TransactionId":"6","s10TransactionIdDate":"20230315","sealAlgorithm":"sha256","transactionPlatform":"PROD","paymentAttemptNumber":2,"preAuthorisationRuleResultList":[{"ruleCode":"VI","ruleType":"NG","ruleWeight":"I","ruleSetting":"S","ruleResultIndicator":"0","ruleDetailedInfo":"TRANS=1:3;CUMUL=24999:200000"},{"ruleCode":"RCode","ruleType":"RType","ruleWeight":"RWeight","ruleSetting":"RSetting","ruleResultIndicator":"RIndicator","ruleDetailedInfo":"DetailedInfo"}]}The Seal you have to obtain is 77be1c230491c0d4eef6eaf910f635d42f55c90cd34c5a162c0ef6fcefb3f087
For the SHA-256 algorithm (although this is the default value, this algorithm is no longer recommended):
- concatenation of the Data field and of the secret key (encoded if the corresponding option is selected)
- UTF-8 encoding of the data constituting the result of the previous operation
- SHA256 hashing of the bytes obtained
This procedure can be summarised as follows:
SHA256( UTF-8(Data+secretKey ) )Example of computed Seal with a secret key equal to "secret123" and the Data field in POST format below:
captureDay=0|captureMode=AUTHOR_CAPTURE|currencyCode=978|merchantId=039000254447216|orderChannel=INTERNET|responseCode=00|transactionDateTime=2022-11-14T11:21:12+01:00|transactionReference=SIM20221114112037|keyVersion=1|acquirerResponseCode=00|amount=1000|authorisationId=664865|guaranteeIndicator=N|panExpiryDate=202401|paymentMeanBrand=VISA|paymentMeanType=CARD|customerIpAddress=10.78.106.18|maskedPan=############0600|holderAuthentRelegation=N|holderAuthentStatus=NOT_PARTICIPATING|tokenPan=490700h719850600|transactionOrigin=SIMS|paymentPattern=ONE_SHOT|customerMobilePhone=null|mandateAuthentMethod=null|mandateUsage=null|transactionActors=null|mandateId=null|captureLimitDate=20221114|dccStatus=null|dccResponseCode=null|dccAmount=null|dccCurrencyCode=null|dccExchangeRate=null|dccExchangeRateValidity=null|dccProvider=null|statementReference=null|panEntryMode=MANUAL|walletType=null|holderAuthentMethod=NO_AUTHENT_METHOD|holderAuthentProgram=3DS_V2|paymentMeanId=null|instalmentNumber=null|instalmentDatesList=null|instalmentTransactionReferencesList=null|instalmentAmountsList=null|settlementMode=null|mandateCertificationType=null|valueDate=null|creditorId=null|acquirerResponseIdentifier=null|acquirerResponseMessage=null|paymentMeanTradingName=null|additionalAuthorisationNumber=null|issuerWalletInformation=null|s10TransactionId=6|s10TransactionIdDate=20221114|preAuthenticationColor=null|preAuthenticationInfo=null|preAuthenticationProfile=null|preAuthenticationThreshold=null|preAuthenticationValue=null|invoiceReference=null|s10transactionIdsList=null|cardProductCode=F|cardProductName=VISA CLASSIC|cardProductProfile=C|issuerCode=00000|issuerCountryCode=GRC|acquirerNativeResponseCode=00|settlementModeComplement=null|preAuthorisationProfile=null|preAuthorisationProfileValue=null|preAuthorisationRuleResultList=[{"ruleCode":"VI","ruleType":"NG","ruleWeight":"I","ruleSetting":"S","ruleResultIndicator":"0","ruleDetailedInfo":"TRANS=1:3;CUMUL=24999:200000"},{"ruleCode":"RCode","ruleType":"RType","ruleWeight":"RWeight","ruleSetting":"RSetting","ruleResultIndicator":"RIndicator","ruleDetailedInfo":"DetailedInfo"}]|preAuthenticationProfileValue=null|preAuthenticationRuleResultList=null|paymentMeanBrandSelectionStatus=NOT_APPLICABLE|transactionPlatform=PROD|avsAddressResponseCode=null|avsPostcodeResponseCode=null|customerCompanyName=null|customerBusinessName=null|customerLegalId=null|customerPositionOccupied=null|paymentAttemptNumber=1|holderContactEmail=null|installmentIntermediateServiceProviderOperationIdsList=null|holderAuthentType=null|acquirerContractNumber=3863090010|secureReference=null|authentExemptionReasonList=null|paymentAccountReference=a667b63d8bec4fb980106497c53e4|schemeTransactionIdentifier=b4e683c1a6ff4a09a0415116a0a25b401d38c19d24e643078d|guaranteeLimitDateTime=null|paymentMeanDataProvider=null|virtualCardIndicator=N|cardProductUsageLabel=CREDIT|authorisationTypeLabel=TRANSACTION DE PAIEMENT|authorMessageReference=272612|acceptanceSystemApplicationId=142000000001|challengeMode3DS=null|issuingCountryCode=GRC|abortedProcessingStep=null|abortedProcessingLocation=nullThe Seal you have to obtain is 8fb7c5b7e972ed5a279629757aeae9885cdfc1fd888e6fc03114064e94bb2bf4
Example of computed Seal with a secret key equal to "secret123" and the Data field in JSON format below:
{"keyVersion":1,"amount":44000,"captureDay":0,"captureMode":"AUTHOR_CAPTURE","currencyCode":"978","customerId":"40813","customerIpAddress":"213.118.246.190","merchantId":"225005049920001","orderAmount":44000,"orderChannel":"INTERNET","responseCode":"97","responseDescription":"Request time-out; transaction refused","transactionDateTime":"2023-03-15.00:39:04+0100","transactionReference":"dd88adfZ1027b40813f40813y1678837075","statementReference":"T7Ft4KKLRA2M11B9","s10TransactionId":"6","s10TransactionIdDate":"20230315","sealAlgorithm":"sha256","transactionPlatform":"PROD","paymentAttemptNumber":2,"preAuthorisationRuleResultList":[{"ruleCode":"VI","ruleType":"NG","ruleWeight":"I","ruleSetting":"S","ruleResultIndicator":"0","ruleDetailedInfo":"TRANS=1:3;CUMUL=24999:200000"},{"ruleCode":"RCode","ruleType":"RType","ruleWeight":"RWeight","ruleSetting":"RSetting","ruleResultIndicator":"RIndicator","ruleDetailedInfo":"DetailedInfo"}]}The Seal you have to obtain is e9aa5be21186a9f9a417b82d1d450792851c849ccc8a2f85136897da29477975
Specifying the manual response URL
The main goal of the manual response is to redirect the customer to your website with the result of the payment so you can make the right decision about it. For instance, if an error occurred, you may suggest to the customer to attempt the payment again. If the payment is successful, you can display a “thank you” message and start despatching the goods.
During the final step, a 'Continue' button is displayed on the Sogenactif payment page, with a link that redirects the user to your site. When the customer clicks on this link, the Sogenactif server redirects them to the URL contained in the normalReturnUrl field supplied in the request. The redirection is a HTTP(s) POST request that contains the data of the response as described above. It is your responsibility to retrieve these parameters and check the signature, thus ensuring the integrity of the response. Besides, you are in charge of displaying relevant messages to your customer (i.e. messages pertaining to the details of the response).
This normalReturnUrl field is also used for all payment results (cancellation, refusal,etc.) so as to perform the redirection to your site.
It is important to note that the receipt of the response cannot be guaranteed, since this response is sent by the customer’s Web browser. First, the customer may choose not to click on the link. Then he might encounter connection issues that block the transmission of this response. Therefore, your business processes cannot be based only on this response.
Specifying the automatic response URL
The automatic response is sent only if the automaticResponseUrl field was sent in the payment request. If that is the case, the Sogenactif server sends a HTTP(S) POST response to the URL address received.
The fields of the automatic response are the same as those of the manual response. The only difference between both procedures is that the automatic response is sent directly by the Sogenactif server and does not go through the customer's Web browser. Therefore, this response is much more reliable since it is always sent. The Sogenactif server does not expect any response after the automatic response has been sent.
It is your responsibility to retrieve the various data of the response, check the signature to make sure the fields of the response have not been tampered with, and update your back office.
The automatic response is sent at the end of the payment. However, if your customer drops their purchase, for example by exiting their browser, the automatic response is sent when the user session expires (after 15 minutes of inactivity). Therefore, if your customer drops their purchase, you will only receive the automatic response (not the manual response), with an answer code set at 97, about 15 to 16 minutes after the customer has been redirected to the payment pages.
If an automatic response is not received after approximately 16 minutes, you can get the result of a payment by calling the getTransactionData method of the Sogenactif Office Serveur interface, or by analysing the contents of the Transactions report. You may also search for a transaction and see its status using Sogenactif Gestion.
Choose response format : POST or JSON
From the interfaceVersion HP_3.0 Sogenactif sends you the concatenated string of the response (Data
field) in 2 distinct formats to choose :
The POST format
This POST format has the following structure : key1=value1|key2=value2…
POST response example with "pipe" separator between the data
captureDay=0|captureMode=AUTHOR_CAPTURE|currencyCode=978|merchantId=039000254447216
|orderChannel=INTERNET|responseCode=00|transactionDateTime=2022-11-14T11:21:12+01:00|transactionReference=SIM20221114112037
|keyVersion=1|acquirerResponseCode=00|amount=1000|authorisationId=664865|guaranteeIndicator=N|panExpiryDate=202401
|paymentMeanBrand=VISA|paymentMeanType=CARD|customerIpAddress=10.78.106.18|maskedPan=############0600|holderAuthentRelegation=N
|holderAuthentStatus=NOT_PARTICIPATING|tokenPan=490700h719850600|transactionOrigin=SIMS|paymentPattern=ONE_SHOT
|customerMobilePhone=null|mandateAuthentMethod=null|mandateUsage=null|transactionActors=null|mandateId=null|captureLimitDate=20221114
|dccStatus=null|dccResponseCode=null|dccAmount=null|dccCurrencyCode=null|dccExchangeRate=null|dccExchangeRateValidity=null
|dccProvider=null|statementReference=null|panEntryMode=MANUAL|walletType=null|holderAuthentMethod=NO_AUTHENT_METHOD
|holderAuthentProgram=3DS_V2|paymentMeanId=null|instalmentNumber=null|instalmentDatesList=null|instalmentTransactionReferencesList=null
|instalmentAmountsList=null|settlementMode=null|mandateCertificationType=null|valueDate=null|creditorId=null
|acquirerResponseIdentifier=null|acquirerResponseMessage=null|paymentMeanTradingName=null|additionalAuthorisationNumber=null
|issuerWalletInformation=null|s10TransactionId=6|s10TransactionIdDate=20221114|preAuthenticationColor=null|preAuthenticationInfo=null
|preAuthenticationProfile=null|preAuthenticationThreshold=null|preAuthenticationValue=null|invoiceReference=null|s10transactionIdsList=null
|cardProductCode=F|cardProductName=VISA CLASSIC|cardProductProfile=C|issuerCode=00000|issuerCountryCode=GRC|acquirerNativeResponseCode=00
|settlementModeComplement=null|preAuthorisationProfile=null|preAuthorisationProfileValue=null
|preAuthorisationRuleResultList=[{"ruleCode":"VI","ruleType":"NG","ruleWeight":"I","ruleSetting":"S","ruleResultIndicator":"0","ruleDetailedInfo":"TRANS=1:3;CUMUL=24999:200000"},{"ruleCode":"RCode","ruleType":"RType","ruleWeight":"RWeight","ruleSetting":"RSetting","ruleResultIndicator":"RIndicator","ruleDetailedInfo":"DetailedInfo"}]
|preAuthenticationProfileValue=null|preAuthenticationRuleResultList=null|paymentMeanBrandSelectionStatus=NOT_APPLICABLE|transactionPlatform=PROD
|avsAddressResponseCode=null|avsPostcodeResponseCode=null|customerCompanyName=null|customerBusinessName=null|customerLegalId=null
|customerPositionOccupied=null|paymentAttemptNumber=1|holderContactEmail=null|installmentIntermediateServiceProviderOperationIdsList=null
|holderAuthentType=null|acquirerContractNumber=3863090010|secureReference=null|authentExemptionReasonList=null
|paymentAccountReference=a667b63d8bec4fb980106497c53e4|schemeTransactionIdentifier=b4e683c1a6ff4a09a0415116a0a25b401d38c19d24e643078d
|guaranteeLimitDateTime=null|paymentMeanDataProvider=null|virtualCardIndicator=N|cardProductUsageLabel=CREDIT|authorisationTypeLabel=TRANSACTION DE PAIEMENT
|authorMessageReference=272612|acceptanceSystemApplicationId=142000000001|challengeMode3DS=null|issuingCountryCode=GRC|abortedProcessingStep=null|abortedProcessingLocation=null(see § Syntax of lists of complex objects in responses)
The JSON format
JSON format has the following structure : { "key1" : "value1", "key2" : "value2", …}
JSON response example
{
"keyVersion": 1, "acquirerResponseCode": "00", "acquirerResponseDescription": "Transaction approved or processed successfully",
"amount": 1000, "authorisationId": "858191", "captureDay": 0, "captureMode": "AUTHOR_CAPTURE", "cardScheme": "VISA",
"chargeAmount": 0, "currencyCode": "978", "customerIpAddress": "10.78.106.18", "guaranteeIndicator": "N",
"holderAuthentRelegation": "N", "holderAuthentStatus": "NOT_PARTICIPATING", "maskedPan": "############0600",
"merchantId": "039000254447216", "orderAmount": 1000, "orderChannel": "INTERNET", "panExpiryDate": "202401",
"paymentMeanBrand": "VISA", "paymentPattern": "ONE_SHOT", "responseCode": "00", "responseDescription": "Process succeeded",
"tokenPan": "490700h719850600", "transactionDateTime": "2022-11-14.11:19:39+0100", "transactionOrigin": "SIMS",
"transactionReference": "SIM20221114111757", "captureLimitDate": "20221114", "paymentMeanType": "CARD", "panEntryMode": "MANUAL",
"holderAuthentMethod": "NO_AUTHENT_METHOD", "holderAuthentProgram": "3DS_V2", "s10TransactionId": "5", "s10TransactionIdDate": "20221114",
"cardProductCode": "F", "cardProductName": "VISA CLASSIC", "cardProductProfile": "C", "issuerCode": "00000", "issuerCountryCode": "GRC",
"acquirerNativeResponseCode": "00", "sealAlgorithm": "sha256", "paymentMeanBrandSelectionStatus": "NOT_APPLICABLE",
"transactionPlatform": "PROD", "paymentAttemptNumber": 1, "acquirerContractNumber": "3863090010",
"schemeTransactionIdentifier": "79e70b862e5942ff86f31951235959a16f45f41f797f48129e",
"paymentAccountReference": "945dbb3e0b984bfc896a04c5bc273", "virtualCardIndicator": "N", "cardProductUsageLabel": "CREDIT",
"authorisationTypeLabel": "TRANSACTION DE PAIEMENT", "authorMessageReference": "179263", "acceptanceSystemApplicationId": "142000000001",
"issuingCountryCode": "GRC", "threeDLiabilityShift": "N", "threeDStatusCode": "NOT_PARTICIPATING", "threeDRelegationCode": "N",
"preAuthorisationRuleResultList":[
{"ruleCode":"VI","ruleType":"NG","ruleWeight":"I","ruleSetting":"S","ruleResultIndicator":"0","ruleDetailedInfo":"TRANS=1:3;CUMUL=24999:200000"},
{"ruleCode":"RCode","ruleType":"RType","ruleWeight":"RWeight","ruleSetting":"RSetting","ruleResultIndicator":"RIndicator","ruleDetailedInfo":"DetailedInfo"}
]
}
Default behaviour since the interfaceVersion
HP_3.0
Format of the automatic and manual response is determined by the connector that was used during HTTPS exchanges between your website and Sogenactif servers
| Interface Version | Connector | Response Format |
|---|---|---|
| IR_WS_3.x | JSON | JSON (JS_3.x) |
| HP_3.x | POST | POST (HP_3.x) |
| IR_WS_3.x | SOAP | POST (HP_3.x) |
Choose response versions from the payment request
If you want to override this default behavior it is possible to fill in from the payment request the exact versions of the automatic and manual responses that you use.
The payment request field which allows to fill in the automatic
response version is interfaceVersionAutomaticResponse
The payment request field which allows to fill in the manual response
version is interfaceVersionNormalResponse
These
two new fields interfaceVersionAutomaticResponse and
interfaceVersionNormalResponse are optional but if one of
both is filled in so the other one becomes mandatory. Otherwise, the
payment initialization request is failed (error code 12).
Solving response receipt issues
Below is a list of the most common issues that block the receipt of automatic and manual responses. Please make sure you have checked them before you call the technical support:
- Make sure the response URLs are provided in the payment request and are valid. To do this, simply copy and paste them into the address bar of your browser.
- The supplied URLs must be accessible from the outside, i.e. the Internet. Access control mechanisms (login/password or IP address filter) or a firewall might block access to your server.
- Access to response URLs must be confirmed in the notifications report of your web browser.
- If you use a non-standard port, it must be within the 80 to 9999 range to ensure compatibility with Sogenactif.
- Context parameters cannot be added to the response URLs. However, some fields can still be used, e.g. the orderID or returnContext fields make it possible to provide extra parameters. You may also use the sessionId field to retrieve information about your customer at the end of the payment process.
In some error cases, the Sogenactif Server is unable to sign the response message. This applies, for instance, to the "Unknown merchantID" error and to the situation where the secret key is unkwown to Sogenactif. For these particular reasons, the payment server will send a response without a signature in the Seal field.
Retrieving response fields
The content of the automatic and manual responses sent by Sogenactif Paypage is identical. This content may vary according to the payment result (successful or other).
The fields present in the automatic and manual responses are listed on this page.
Optional fields pertaining to fraud checks
- Content of preAuthenticationRuleResult
| Field | Version | Comments |
|---|---|---|
| ruleCode | HP_2.14 | |
| ruleType | HP_2.14 | |
| ruleWeight | HP_2.14 | |
| ruleSetting | HP_2.14 | |
| ruleResultIndicator | HP_2.14 | |
| ruleDetailedInfo | HP_2.14 |
- Content of preAuthorisationRuleResult
| Field | Version | Comments |
|---|---|---|
| ruleCode | HP_2.14 | |
| ruleType | HP_2.14 | |
| ruleWeight | HP_2.14 | |
| ruleSetting | HP_2.14 | |
| ruleResultIndicator | HP_2.14 | |
| ruleDetailedInfo | HP_2.14 |
Syntax of lists of complex objects in responses
The format of a list of complex objects in automatic and manual responses is defined as follows (bold text):
..|amount=1000|currencyCode=978|objectNameList=[{"field1":"value1a",
"field2":"value2a","field3":"value3a"…},{"field1":"value1b",
"field2":"value2b","field3":"value3b"}…]|transactionReference=1452687287828|..- The content of the list is in square brackets [ ].
- Each entry of the list is in curly brackets { }.
- Each field is represented as "fieldName" = "fieldValue".
- Please note that the name and the value of the field are both in double quotes "".
- Pairs of adjacent names/values are separated by a comma.
Sample preAuthorisationRuleResultList field
Breakdown of the fraud rules executed during preauthorisation (bold text):
..|amount=1000|currencyCode=978|preAuthorisationRuleResultList=[
{”ruleCode”:"SC",”ruleType”:"NG",”ruleWeight”:"I",”ruleSetting”:"S",
”ruleResultIndicator”:"0",“ruleDetailedInfo”:"TRANS=1:5;
CUMUL=1000:99999900"},{”ruleCode”:"GC",”ruleType”:"NG",”ruleWeight”:
"D",”ruleSetting”:"N",”ruleResultIndicator”:"0",“ruleDetailedInfo”:
""},{”ruleCode”:"CR",”ruleType”:"NG",”ruleWeight”:"D",”ruleSetting”
:"S",”ruleResultIndicator”:"N",“ruleDetailedInfo”:"CARD_COUNTRY=USA"}]
|transactionReference=1452687287828|..Payment response analysis
If you carry out the authentication steps by means of an electronic seal, you should make sure the seal you received actually matches the seal you recomputed using the response fields.
In case the seal you received does not match the seal you recomputed, the transaction status is considered unknown, please leave the transaction as it is, contact the support and do not re-execute the transaction in any automated way.
| Status | Response fields | Actions to be carried out | |
|---|---|---|---|
Payment accepted |
responseCode = 00 acquirerResponseCode = 00 guaranteeIndicator = Y,N,U, empty |
You can deliver the order according to the guarantee level of your choosing (guaranteeIndicator field). |
|
Sogenactif fraud refusal Go-No-Go |
responseCode = 05 complementaryCode = XX preAuthorisationRuleResultList |
The payment has been refused by the Sogenactif fraud engine that you configured. Do not deliver the goods. Analyse in detail the fraud rules executed by Sogenactif to know the reason for the refusal (preAuthorisationRuleResultList field). |
|
Sogenactif fraud refusal Scoring |
responseCode = 05 scoreColor = RED, BLACK scoreValue = X (transaction score) scoreThreshold = X,Y (orange threshold, green threshold) |
The payment has been refused by the Sogenactif fraud engine that you configured. Do not deliver the goods. Analyse in detail the fraud rules executed by Sogenactif to know the reason for the refusal (preAuthorisationRuleResultList field). |
|
Sogenactif fraud warning Scoring |
responseCode = 05 scoreColor = ORANGE scoreValue = X (transaction score) scoreThreshold = X,Y (orange threshold, green threshold) |
The acquirer has authorised the payment, but the Sogenactif fraud engine issued a warning due to the rules you configured. Analyse in detail the fraud rules executed by Sogenactif to know the reason for the warning (preAuthorisationRuleResultList field). If the transaction poses no risk, accept it using the acceptChallenge function. If the transaction poses a risk, refuse it using the refuseChallenge function. The acceptChallenge and refuseChallenge functions are available on the extranet and the Sogenactif Office Serveur connectors. |
|
3-D Secure refusal |
reponseCode = 05 holderAuthenStatus = FAILURE |
Customer authentication failed. This is not necessarily due to fraud. You can suggest to your customer to attempt the payment again with another means of payment, by generating a new request. |
|
Banking refusal from the acquirer |
responseCode = 05 acquirerResponseCode = XX |
Authorisation refused for a reason not related to fraud. You can suggest to your customer to attempt the payment again with another means of payment, by generating a new request. |
|
| Soft decline | responseCode = 05 acquirerResponseCode = A1 |
The payment has been refused by the acquirer because the
3-D Secure data is missing in the authorisation
request. Please try to pay again with a 3-D Secure payment
process. |
|
Fraud refusal from the acquirer |
responseCode = 34 acquirerResponseCode = XX |
Authorisation refused because of fraud. Do not deliver the order. |
|
Refusal because the maximum number of attempts has been reached |
responseCode = 75 acquirerResponseCode = XX |
The customer made several failed attempts because the information entered was incorrect. There are two possibilities:
Please contact your customer to define what to do next. |
|
Refusal due to a technical issue |
responseCode = 90, 99 acquirerResponseCode = 90 to 98 |
Temporary technical issue while processing the transaction. Please tell your customer to attempt the payment again later. |
|
| Abandonment of payment | responseCode = 97 acquirerResponseCode = not filled |
Do not deliver the order. |
Step 3: testing in the simulation environment
Once you have developed the connection to Sogenactif Paypage, you can do a test on the Sogenactif Paypage simulation server.
To do this test, you must use the credentials according to the transaction identification mode you wish to use:
| Simulation server URL https://payment-webinit.simu.sogenactif.com/paymentInit |
| Field | Value |
|---|---|
| Merchant ID (merchantId) | 002010000000002 |
| Secret key (secretKey) | 002010000000002_KEY1 |
| Key version (keyVersion) | 1 |
| Field | Value |
|---|---|
| Merchant ID (merchantId) | 002010000000001 |
| Secret key (secretKey) | 002010000000001_KEY1 |
| Key version (keyVersion) | 1 |
| Field | Value |
|---|---|
| Merchant ID (merchantId) | 002010000000003 |
| Secret key (secretKey) | 002010000000003_KEY1 |
| Key version (keyVersion) | 1 |
| Field | Value |
|---|---|
| Merchant ID (merchantId) | 002010000000004 |
| Secret key (secretKey) | 002010000000004_KEY1 |
| Key version (keyVersion) | 1 |
This simulation server is not connected to the actual banking servers, because it serves to validate the connection between your website and the payment server.
Therefore, Sogenactif Paypage simulates the call to the authorisation servers so you can test the various results of a payment.
Consequently, using actual cards is not necessary for tests.
You use a generic shop without any payment page customisation. Step 4 will enable you to customise your payment pages.
Testing CB, VISA, MASTERCARD and AMEX transactions
The following simulation rules apply:
- The PAN (Primary Account Number) must consist of 15 to 19 digits (depending on the means of payment used).
- The first six digits of the PAN determine the type of card as per
the table below.
Card type Card number begins with AMEX 340000 VPAY 400000 VISA 410000 CB 420000 CB-VISA co-branded cards 430000 CB-VPAY co-branded cards 440000 CB-VISA_ELECTRON co-branded cards 450000 VISA-MASTERCARD co-branded cards 460000 MAESTRO 500000 MASTERCARD 510000 CB-MASTERCARD co-branded cards 520000 CB-MAESTRO co-branded cards 530000 - The Sogenactif response code (responseCode field) is computed from the last two digits of the card number.
- The security code (CVV) consists of 3 or 4 digits. This value does not matter when it comes to the result of the simulation.
Example: if you use the card number 4100 0000 0000 0005, the card will be identified as a VISA card and the payment will be refused (Sogenactif response code 05).
Co-branded cards can be used with every brand defined in the table.
All cards are enrolled in the 3-D Secure programme. You will be redirected to the 3-D Secure simulation server on which you will choose the desired 3-D Secure authentication result.
Testing iDeal transactions
If you choose to test iDeal, you will be redirected to the simulation server that simulates iDeal transactions according to their amounts. You will then be taken back to the payment server that will display the receipt showing the transaction result.
Rules for simulating iDeal payments:
| Transaction amount | iDeal response |
|---|---|
| EUR2.00 | Transaction cancelled |
| EUR3.00 | Transaction expired |
| EUR4.00 | Transaction not carried out |
| EUR5.00 | Transaction failed |
| Other cases | Transaction OK |
Testing PayPal transactions
If you choose to test PayPal, you will be redirected to the simulation server that simulates PayPal transactions according to their payment result on PayPal’s side. You will then be taken back to the payment server that will display the receipt showing the result of the payment.
Step 4: validating the switch to the production environment
Once you have tested your website connection to Sogenactif Paypage POST, you can validate the connection to the production version of Sogenactif Paypage POST.
Prior to this, we recommend you block public access to your website to prevent customers from carrying out transactions during this validation phase.
If you would like to customise your payment pages, you can use our Sogenactif CustomPages tool to test and view the rendering on payment pages. To do so, please refer to the Sogenactif CustomPages documentation to use the tool.
To switch to the production server, you must change the URL in order to connect to the Sogenactif production server using the merchantId, secretKey and keyVersion credentials you received during the registration phase.
| Sogenactif URL | https://payment-web.sogenactif.com/paymentInit |
| merchantId | Shop identifier received by e-mail |
| SecretKey | Secret key you can retrieve from the Sogenactif Téléchargement extranet |
| keyVersion | Secret key version retrieved from Sogenactif Téléchargement (obviously 1 for the first key) |
How to validate the proper functioning in the production environment
Immediately:
- Make a transaction using a real payment card (your own, if possible). If the transaction is accepted, it will be sent to the bank to credit your merchant account and to debit the card account.
- Check that your payment pages include your customisation settings.
- Check the transaction via Sogenactif Gestion, using the transactionReference.
The next day:
- Make sure the transaction is in the Transactions report.
- Check your account to make sure the operation was credited.
- Refund the transaction via Sogenactif Gestion (optional).
Two days later:
- Check that the refund transaction is in the Operations report.
- Make sure the debited amount has been refunded to your merchant account.
This validation process is also applicable to the PayPal means of payment.
Step 5: launching live operation
Once the validation for the transition to live operation has been carried out, make your site and/or application public so your customers can make purchases and payments.
On the same day:
- Monitor acceptance rates (number of responseCode 00 per total number of transactions)
- Check the nature of non-banking declines:
- technical issue: responseCode 90, 99
- fraud: responseCode 34
- maximum number of payment attempts reached: responseCode 75
- abandonment: responseCode 97
The next day:
- Check that all transactions processed (accepted and refused) are in the Transactions report.
- Check the operations you have carried out and remittances (report option) in the Operations report.